Three guys hacked an FIA website and accessed Max Verstappen’s passport…
With just a few lines of JavaScript.

Here's what happened.
F1 drivers don’t just race in F1. They sometimes jump into other motorsports.

Max Verstappen, an F1 driver, racing in GT3
To keep it fair, the FIA uses driver categories (kind of like ranking):

F1 drivers, for example, are categorized as Platinum.
Now, this whole system is managed through the official FIA website.
And here’s where it gets wild.
Three researchers, Ian Carroll, Gal Nagli & Sam Curry, tested the website’s security for fun.



And somehow... that little experiment got them Max Verstappen’s passport.

When you log in as a driver, you upload your private documents for categorization.

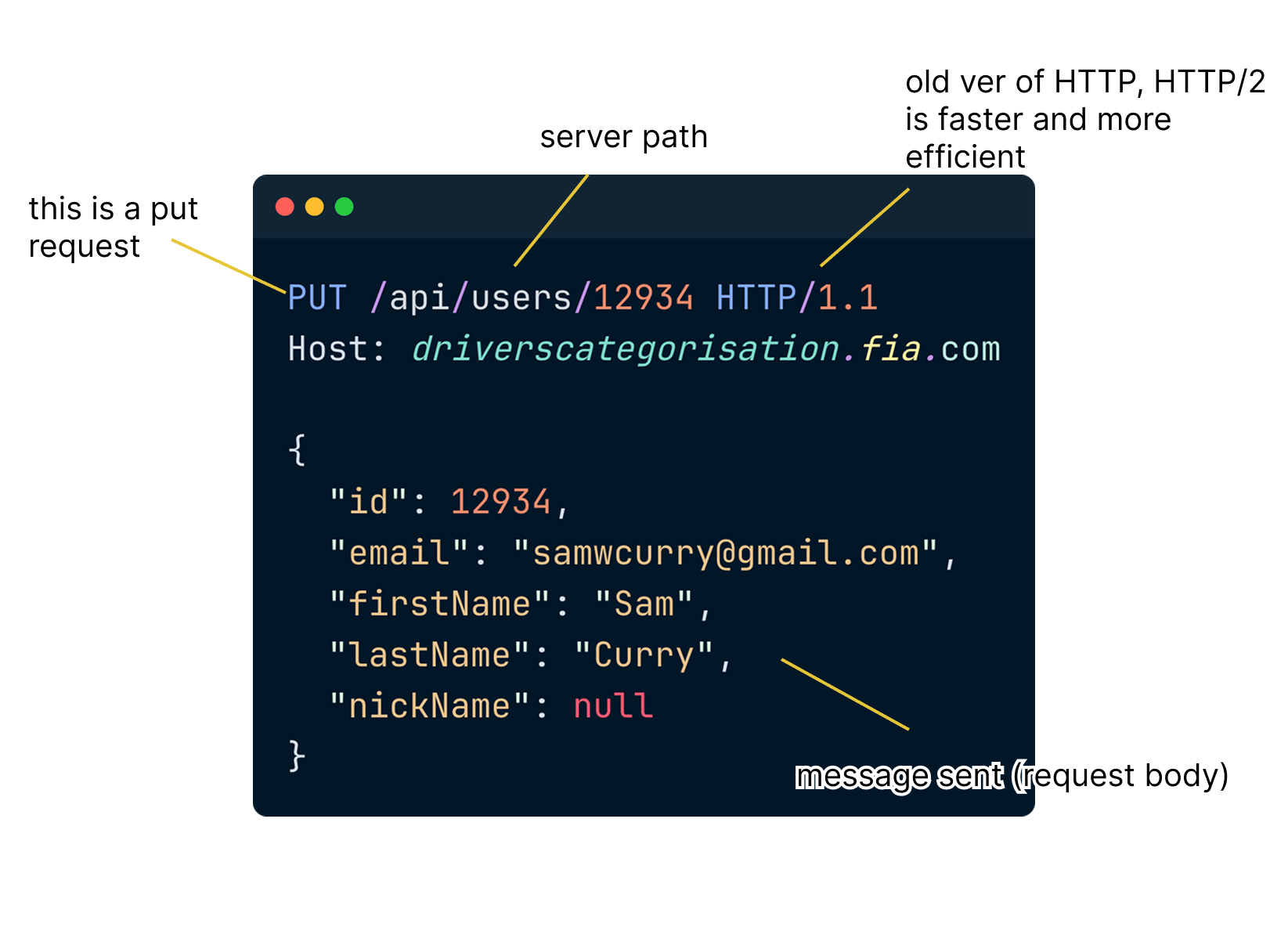
The researchers found that a simple HTTP PUT request is used to update your profile.
What’s interesting is that the JSON response had a field called "role.”
HTTP/1.1 200
Content-type: application/json
{
//other fields
"roles": null,
}So they thought, “What if we just give ourselves an admin role?”
And they did. They reverse-engineered the request format from the website’s JavaScript…
Sent the PUT request…
PUT /api/users/12934 HTTP/1.1
{
"roles": [
{
"id": 1,
"description": "ADMIN role",
"name": "ADMIN"
}
]
}And get full admin access to the website.

Now they could see everything.
Max Verstappen’s passport, his racing license, his resume…
While they didn't do anything evil and reported it to the FIA, it’s insane how a tiny security flaw could expose a billion-dollar organization.
